New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Enhance login security - Return same generic error for invalid user or password #101
Comments
|
Thanks for submitting this. I'm open to feedback from more people, but this was a conscious design decision to prioritize usability over obfuscation, particularly because:
But again, I'm open to any further input. |
|
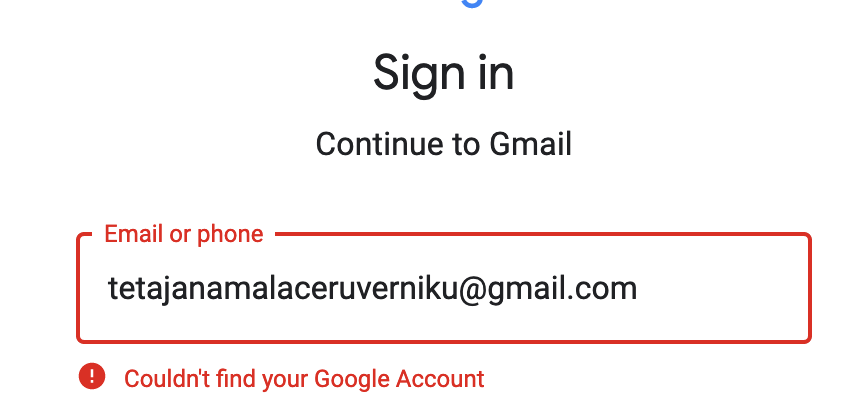
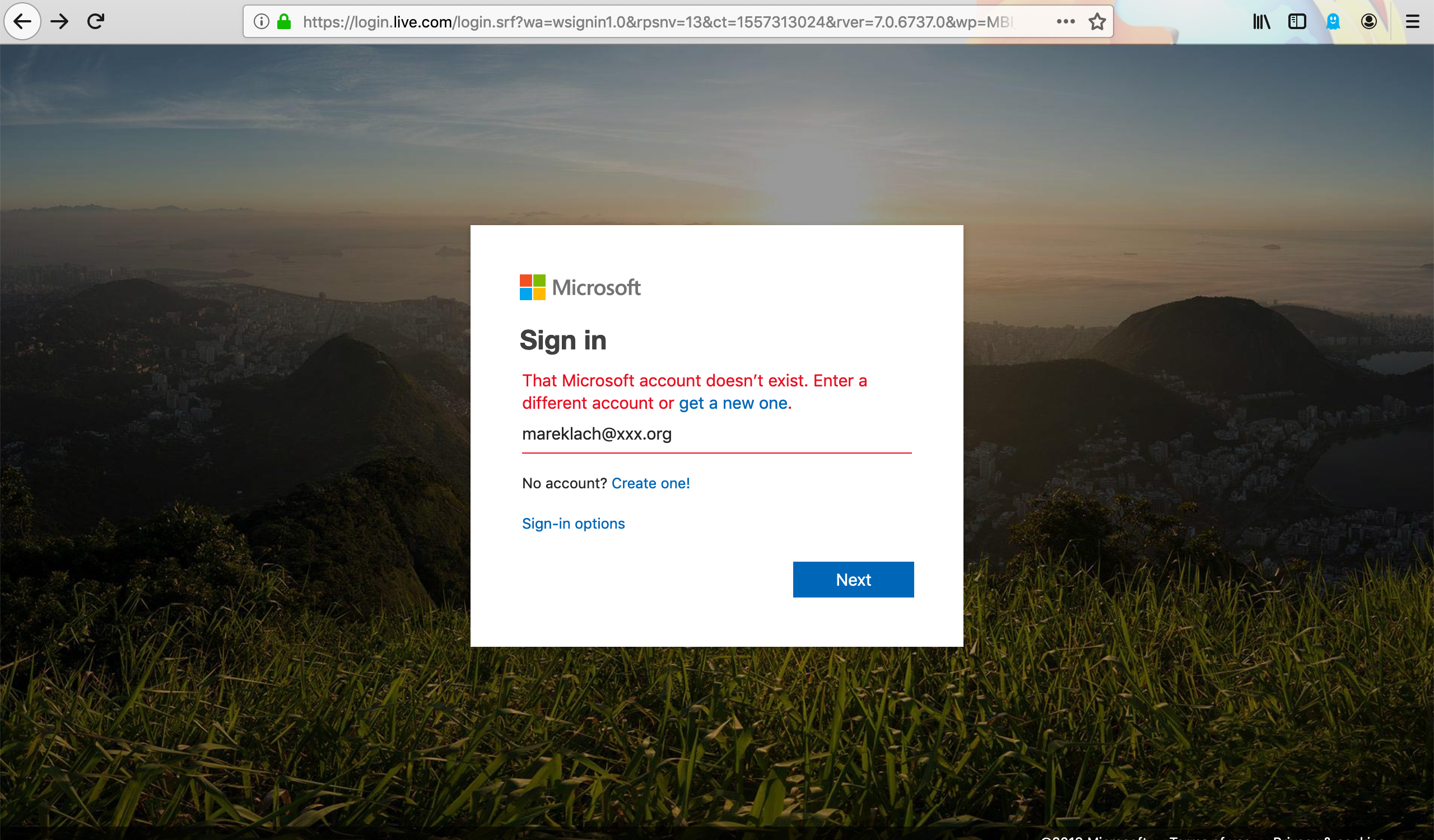
Google's login process is that if you put in a correct email username, it will automatically accept it and then you just have to enter the password. If your email handle is wrong it'll say so: Microsoft's Live Outlook.com service is very similar to how they handle this, telling the user if they have entered the right login first, and only then asking for a password: There's an alternative option to cosider where 'forgot password' would just ask for the user's email address, and then the received email would be like: Hello [username], Renew your password by clicking here: [password reset link] |
|
Great points, @marek-lach. Thanks for the input. It seems the current design is optimal, so I'll go ahead and close this. |
Describe the bug
Login attempts expose if the username is wrong
Steps to reproduce (if necessary)
Steps to reproduce the behavior:
Expected behavior
Return the same generic error message if username or password is wrong, so it's not as easy to get the login.
Application configuration
N/A
Version or last commit:
0.9.1
The text was updated successfully, but these errors were encountered: